In many cases, people do not understand the difference between a Red Team Assessment, a Penetration Testing, and a Vulnerability Assessment. To get the best outcome and value for Your money, You need to understand what are Your goals and then choose the best suitable assessment. While all of them have similar concepts, they are still quite different and fulfill different purpose. Below is Threat Pyramid that shows general difference of each assessment.
Vulnerability Assessment – Why, What and How:
- Maps outdated software and misconfigurations with automated tools.
- Helps to detect, identify, categorize, and manage vulnerabilities and weaknesses in IT systems. These include lacking patches, insecure configurations, end-of-life detection for software or hardware, and other possible missing security-related updates.
- Vulnerability assessments can be internal or external. The main idea behind external vulnerability assessment is to detect exposed and vulnerable systems visible from the internet. It helps to reduce possible incidents and accidental data leakage. In addition, an internal scan is needed to cover systems that are visible only from company’s internal network.
Penetration Testing – Why, What, and How:
- Takes vulnerability assessments to the next level by exploiting manually and proving out attack paths. The goal of a penetration test is to execute an attack against a target system to identify all its weaknesses.
- Gathers valuable insight about the strengths and weaknesses of the system or application.
- Addresses vulnerabilities throughout the development lifecycle in a timely fashion.
- Avoid sensitive data leakage and system or application being compromised by cybercriminals.
- Receive a thorough report with a summary of vulnerabilities for executives and managers.
- Receive a detailed report about findings, including remediation guidance and recommendations.
Penetration Testing – Testing types
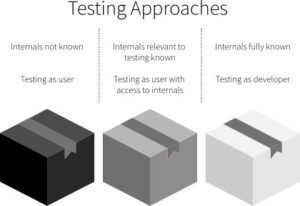
Source: https://www.ranorex.com/black-box-testing-tools/
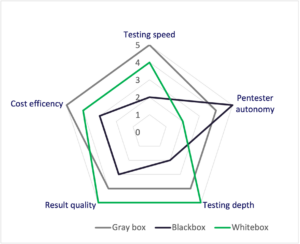
Source:https://www.vaadata.com/blog/black-grey-or-crystal-box-web-pen-testing-3-different-options/
Red Teaming – Why, What and How:
- Real-life experience for your company staff and its security. Test Your security team, defense tools, processes and techniques, systems’ detection, and response capabilities to identify gaps in the defense.
- The blue team (company staff) will get notes from attackers after the exercise.
- The company will be attacked as hackers would do it.
- Helps identify systems for penetration testing.
- Emulated experience is cheaper than real-life intrusions.
- Justify investments in security.
Differences Between Penetration Testing and Red Teaming
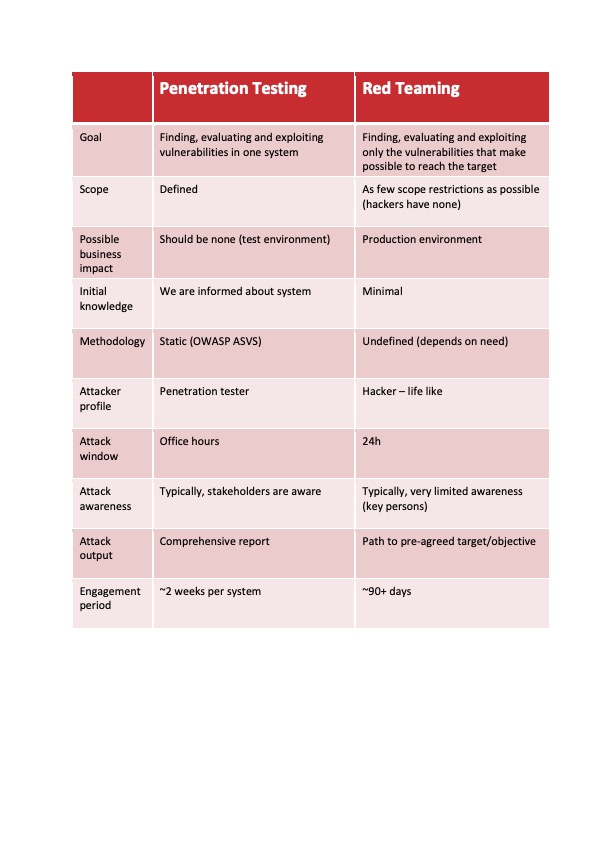
Summary
Neither penetration testing, red teaming nor vulnerability assessment is a “silver bullet”, it depends on what You want to achieve with the testing. Vulnerability scanning helps to detect, identify, categorize, and manage easily to detect vulnerabilities and weaknesses in Your environment. After the easiest “low hanging fruits” are covered, the penetration testing option is good for deep-dive exploration. And finally, red teaming is when there is a need to test the organization as a whole. CYBERS will help You out! Contact us!


